Conference Papers (Recent)
2023
Federated Linear Bandits with Finite Adversarial Actions
L. Fan, R. Zhou, C. Tian, and C. Shen, Thirty-seventh Conference on Neural Information Processing Systems (NeurIPS), Dec. 2023MIMO Beamforming and Signal Modulation Design for Federated Learning Optimization
N. Yang, S. Wang, M. Chen, C. Shen, C. Yin, and C. G. Brinton, IEEE Global Communications Conference (Globecom), Dec. 2023Offline Reinforcement Learning for Wireless Network Optimization with Mixture Datasets
K. Yang, C. Shen, J. Yang, S. Yeh, and J. Sydir, The 57th Asilomar Conference on Signals, Systems and Computers, Oct. 2023. (Invited Paper)Provably Efficient Offline Reinforcement Learning with Perturbed Data Sources
C. Shi, W. Xiong, C. Shen, and J. Yang, International Conference on Machine Learning (ICML), July 2023.Near-optimal Conservative Exploration in Reinforcement Learning under Episode-wise Constraints
D. Li, R. Huang, C. Shen, and J. Yang, International Conference on Machine Learning (ICML), July 2023.Reward Teaching for Federated Multi-Armed Bandits
C. Shi, W. Xiong, C. Shen, and J. Yang, IEEE International Symposium on Information Theory (ISIT), June 2023.On High-Dimensional and Low-Rank Tensor Bandits
C. Shi, C. Shen, and N. D. Sidiropoulos, IEEE International Symposium on Information Theory (ISIT), June 2023.Exploiting Feature Heterogeneity for Improved Generalization in Federated Multi-Task Learning
R. Liu, J. Yang, and C. Shen, IEEE International Symposium on Information Theory (ISIT), June 2023.Nearly Minimax Optimal Offline Reinforcement Learning with Linear Function Approximation: Single-Agent MDP and Markov Game
W. Xiong, H. Zhong, C. Shi, C. Shen, L. Wang, and T. Zhang, International Conference on Learning Representations (ICLR), May 2023Communication and Storage Efficient Federated Split Learning
Y. Mu and C. Shen, IEEE International Conference on Communications (ICC), May 2023.FLORAS: Differentially Private Wireless Federated Learning Using Orthogonal Sequences
X. Wei, T. Wang, R. Huang, C. Shen, J. Yang, and H. V. Poor, IEEE International Conference on Communications (ICC), May 2023.Teaching Reinforcement Learning Agents via Reinforcement Learning
K. Yang, C. Shi, and C. Shen, 57th Annual Conference on Information Sciences and Systems (CISS), March 2023. (Invited Paper)Federated Learning via Indirect Server-Client Communications
J. Bian, C. Shen, and J. Xu 57th Annual Conference on Information Sciences and Systems (CISS), March 2023. (Invited Paper)
2022
Multi-Agent Reinforcement Learning for Wireless User Scheduling: Performance, Scalablility, and Generalization
K. Yang, D. Li, C. Shen, J. Yang, S. Yeh, and J. Sydir, The 56th Asilomar Conference on Signals, Systems and Computers, Oct. 2022. (Invited Paper)A Self-Play Posterior Sampling Algorithm for Zero-Sum Markov Games
W. Xiong, H. Zhong, C. Shi, C. Shen, and T. Zhang, The 39th International Conference on Machine Learning (ICML), July 2022. (acceptance rate: 21.9%)Optimizing Federated Averaging Over Fading Channels
Y. Mu, C. Shen, and Y. C. Eldar, IEEE International Symposium on Information Theory (ISIT), June 2022.Cascading Bandits With Two-Level Feedback
D. Cheng, R. Huang, C. Shen, and J. Yang, IEEE International Symposium on Information Theory (ISIT), June 2022.On Federated Learning with Energy Harvesting Clients
C. Shen, J. Yang, and J. Xu, IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), May 2022. (Invited Paper)Random Orthogonalization for Federated Learning in Massive MIMO Systems
X. Wei, C. Shen, J. Yang, and H. V. Poor, IEEE International Conference on Communications (ICC), May 2022.Learning for Robust Combinatorial Optimization: Algorithm and Application
Z. Shao, J. Yang, C. Shen and S. Ren, IEEE Conference on Computer Communications (INFOCOM), May 2022. (acceptance rate: 19.9%)On the Convergence of Hybrid Federated Learning with Server-Clients Collaborative Training
K. Yang an C. Shen, 56th Annual Conference on Information Sciences and Systems (CISS), March 2022. (Invited Paper)
2021
(Almost) Free Incentivized Exploration from Decentralized Learning Agents
C. Shi, H. Xu, W. Xiong, and C. Shen, Thirty-fifth Conference on Neural Information Processing Systems (NeurIPS), Dec. 2021. (acceptance rate: 26%)Heterogeneous Multi-player Multi-armed Bandits: Closing the Gap and Generalization
C. Shi, W. Xiong, C. Shen, and J. Yang, Thirty-fifth Conference on Neural Information Processing Systems (NeurIPS), Dec. 2021. (acceptance rate: 26%)Federated Linear Contextual Bandits
R. Huang, W. Wu, J. Yang, and C. Shen, Thirty-fifth Conference on Neural Information Processing Systems (NeurIPS), Dec. 2021. (acceptance rate: 26%)A Machine Learning Approach for Rate Prediction in Multicast File-stream Distribution Networks
Y. Mu, Y. Tan, M. Veeraraghavan, and C. Shen, IEEE Global Communications Conference (GLOBECOM), Dec. 2021.An Attackability Perspective on No-Sensing Adversarial Multi-player Multi-armed Bandits
C. Shi and C. Shen, IEEE International Symposium on Information Theory (ISIT), July 2021.Federated Learning over Noisy Channels
X. Wei and C. Shen, IEEE International Conference on Communications (ICC), June 2021.On Energy Efficient Uplink Multi-User MIMO with Shared LNA Control
C. Shen, P. Zhao, and X. Luo, IEEE International Conference on Communications (ICC), June 2021.Design and Analysis of Uplink and Downlink Communications for Federated Learning
S. Zheng, C. Shen, and X. Chen, IEEE International Conference on Communications (ICC), June 2021. (Best Paper Award)SDF-Bayes: Cautious Optimism in Safe Dose-Finding Clinical Trials with Drug Combinations and Heterogeneous Patient Groups
H. Lee, C. Shen, W. Zame, J. Lee, and M. van der Schaar, The 24rd International Conference on Artificial Intelligence and Statistics (AISTATS), Apr. 2021.Federated Multi-armed Bandits with Personalization
C. Shi, C. Shen, and J. Yang, The 24rd International Conference on Artificial Intelligence and Statistics (AISTATS), Apr. 2021. (Oral Presentation, 48/1527 = 3%) [Code]Federated Multi-Armed Bandits
C. Shi and C. Shen, The 35th AAAI Conference on Artificial Intelligence (AAAI), Feb. 2021. [Code] (acceptance rate: 21.4%)
2020
Robust Recursive Partitioning for Heterogeneous Treatment Effects with Uncertainty Quantification
H.-S. Lee, Y. Zhang, W. Zame, C. Shen, J.-W. Lee, and M. van der Schaar, Thirty-fourth Conference on Neural Information Processing Systems (NeurIPS), Dec. 2020. (acceptance rate: 20.1%)Federated Learning with Heterogeneous Quantization
C. Shen and S. Chen, ACM/IEEE Symposium on Edge Computing - Workshop on Edge Computing and Communications (EdgeComm), Nov. 2020.MIMO Receive Antenna Selection via Deep Learning and Greedy Adaptation
C. Shen, D. Li, and J. Yang, The 54th Asilomar Conference on Signals, Systems and Computers, Nov. 2020. (Invited Paper)Thresholded Wirtinger Flow for Fast Millimeter Wave Beam Alignment
C. Gan, J. Yang, and C. Shen, The 54th Asilomar Conference on Signals, Systems and Computers, Nov. 2020. (Invited Paper)Learning for Dose Allocation in Adaptive Clinical Trials with Safety Constraints
C. Shen, Z. Wang, S. Villa, and M. van der Schaar, The 37th International Conference on Machine Learning (ICML), July 2020. (acceptance rate: 21.8%)On Top-
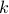 Selection from
Selection from 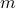 -wise Partial Rankings via Borda Counting
-wise Partial Rankings via Borda Counting
W. Chen, R. Zhou, C. Tian, and C. Shen, IEEE International Symposium on Information Theory (ISIT), June 2020.Deep Reinforcement Learning based Wireless Network Optimization: A Comparative Study
K. Yang, C. Shen, and T. Liu, IEEE INFOCOM 2020 Workshop on Data Driven Intelligence for Networks, July 2020.Contextual Constrained Learning for Dose-Finding Clinical Trials
H. Lee, C. Shen, J. Jordon, and M. van der Schaar, The 23rd International Conference on Artificial Intelligence and Statistics (AISTATS), Aug. 2020.Decentralized Multi-player Multi-armed Bandits with No Collision Information
C. Shi, W. Xiong, C. Shen, and J. Yang, The 23rd International Conference on Artificial Intelligence and Statistics (AISTATS), Aug. 2020.Stochastic Linear Contextual Bandits with Diverse Contexts
W. Wu, J. Yang, and C. Shen, The 23rd International Conference on Artificial Intelligence and Statistics (AISTATS), Aug. 2020.
2019
Privacy-Aware Edge Computing Based on Adaptive DNN Partitioning
C. Shi, L. Chen, C. Shen, and J. Xu, IEEE Global Communications Conference (GLOBECOM), Dec. 2019.A Cascading Bandit Approach to Efficient Mobility Management in Ultra-Dense Networks
C. Wang, R. Zhou, J. Yang, C. Shen, IEEE International Workshop on Machine Learning for Signal Processing, Oct. 2019. (Invited Paper)Power Control for Interference Management via Ensembling Deep Neural Networks
F. Liang, C. Shen, W. Yu, and F. Wu, IEEE/CIC International Conference on Communications in China (ICCC), Changchun, China, Aug. 2019. (Invited Paper)Online Learning with Diverse User Preferences
C. Gan, J. Yang, R. Zhou, and C. Shen, IEEE International Symposium on Information Theory, Paris, France, July 2019.
2018
Best Arm Identification for Both Stochastic and Adversarial Multi-armed Bandits
H. Zhang and C. Shen, IEEE Information Theory Workshop (ITW), Guangzhou, China, Nov. 2018. (Invited Paper)Opportunistic Spectrum Access via Good Arm Identification
Z. Wang, Z. Ying, and C. Shen, IEEE GlobalSIP, Anaheim, California, USA, Nov. 2018.A Machine Learning Approach to User Association in Enterprise Small Cell Networks
J. Yang, C. Wang, X. Wang, and C. Shen, IEEE/CIC International Conference on Communications in China (ICCC), Beijing, China, Aug. 2018. (Invited Paper)Cost-aware Cascading Bandits
R. Zhou, C. Gan, J. Yang, and C. Shen, Proceedings of the Twenty-Seventh International Joint Conference on Artificial Intelligence (IJCAI-18), Pages 3228-3234, July 2018. (acceptance rate: 20.5%)New Results On Multilevel Diversity Coding with Secure Regeneration
S. Shao, T. Liu, C. Tian, and C. Shen, IEEE International Symposium on Information Theory (ISIT), 2018.Regional Multi-Armed Bandits
Z. Wang, R. Zhou, and C. Shen, Proceedings of the Twenty-First International Conference on Artificial Intelligence and Statistics (AISTATS), Playa Blanca, Lanzarote, Canary Islands, April 2018.Small Cell Power Assignment with Unimodal Continuum-armed Bandit Learning
Z. Wang and C. Shen, IEEE International Conference on Communications (ICC) 2018 Workshop on 5G-UDNDesigning Interdependent Networks Against Cascading Failures with Node Protections
K. Liu, C. Shen, S. Chattopadhyay, and H. Dai, IEEE International Conference on Communications (ICC), 2018.A Non-Stationary Online Learning Approach to Mobility Management
Y. Zhou, C. Shen, X. Luo, and M. van der Schaar, IEEE International Conference on Communications (ICC), 2018.Exploiting Noise Correlation for Channel Decoding with Convolutional Neural Networks
F. Liang, C. Shen, and F. Wu, IEEE International Conference on Communications (ICC), 2018.Online Geographical Load Balancing for Energy-Harvesting Mobile Edge Computing
H. Wu, L, Chen, C. Shen, W. Wen, and J. Xu, IEEE International Conference on Communications (ICC), 2018.How to Interconnect for Massive MIMO Self-Calibration?
F. Yang, H. Zhu, C. Shen, L. Dai, and X. Luo, IEEE ICASSP, Calgary, Canada, April 2018.Adaptive Resource Allocation for LTE/WiFi Coexistence in the Unlicensed Spectrum
J. Dai and C. Shen, IEEE International Conference on Computing, Networking and Communications (ICNC), March 2018.
2017
Modified LBT Mechanism and Performance Enhancement for LTE-U/WiFi Co-Existence
J. Dai and C. Shen, IEEE/CIC International Conference on Communications in China (ICCC), 2017.Aligning DL Paths for Scalable CSI Feedback in FDD Massive MIMO
X. Luo, P. Cai, X. Zhang, C. Shen, and H. Qian, Proc. International Wireless Communications and Mobile Computing Conference (IWCMC), Valencia, Spain, June 2017.DL CSI Acquisition and Feedback in FDD Massive MIMO via Path Aligning
X. Luo, X. Zhang, P. Cai, C. Shen, D. Hu, and H. Qian, The 9th International Conference on Ubiquitous and Future Networks, July 2017. (Excellent Paper Award)On the Tradeoff Region of Secure Exact-Repair Regenerating Codes
S. Shao, T. Liu, C. Tian, and C. Shen, IEEE International Symposium on Information Theory (ISIT), Germany, June 2017.On Scheduling Policies in the Presence of Heavy-Tailed Interference
H. Wu, C. Shen, and S. Chen, Proc. Information Theory and Applications (ITA) Workshop, La Jolla, CA, USA, Feb. 2017
